I’ve recently been playing around with VMware’s REST APIs in VCSA 6.5 using PowerShell. I’ve been using a lot of Invoke-WebRequest and Invoke-RestMethod to do my work. Chris Wahl has a great primer on how to get started here.
One issue that I ran into very quickly working again my VCSA was a certificate trust relationship error. I’ve run into this error numerous times in the past.
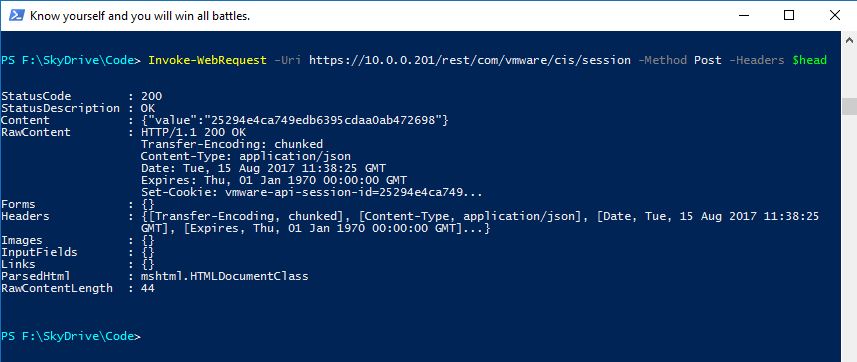
PS F:\Code> Invoke-WebRequest -Uri https://10.0.0.201/rest/com/vmware/cis/session -Method Post -Headers $head Invoke-WebRequest : The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel. At line:1 char:1 + Invoke-WebRequest -Uri https://10.0.0.201/rest/com/vmware/cis/session ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidOperation: (System.Net.HttpWebRequest:HttpWebRequest) [Invoke-WebRequest], WebException + FullyQualifiedErrorId : WebCmdletWebResponseException,Microsoft.PowerShell.Commands.InvokeWebRequestCommand
The first time I ran into this error I was stumped for while finding a solution. Ultimately it comes down to using Self-Signed Certificates in vCenter, as most of us do. In general using Invoke-WebRequest or Invoke-RestMethod against a server using a Self-Signed Certificate will cause this error, it’s not just related to vCenter.
The solution is quite simple. I found a snippet of code some time back that I keep on hand in this situation. It basically ignores certificate validate in PowerShell allowing you to make a connection with Invoke-WebRequest. All you have to do it paste this code into your PowerShell session before you run Invoke-WebRequest against a server with a Self-Signed Certificate.
if (-not ([System.Management.Automation.PSTypeName]'ServerCertificateValidationCallback').Type)
{
$certCallback = @"
using System;
using System.Net;
using System.Net.Security;
using System.Security.Cryptography.X509Certificates;
public class ServerCertificateValidationCallback
{
public static void Ignore()
{
if(ServicePointManager.ServerCertificateValidationCallback ==null)
{
ServicePointManager.ServerCertificateValidationCallback +=
delegate
(
Object obj,
X509Certificate certificate,
X509Chain chain,
SslPolicyErrors errors
)
{
return true;
};
}
}
}
"@
Add-Type $certCallback
}
[ServerCertificateValidationCallback]::Ignore()
Once you run the code you will be able to now successfully make a connection.
I’ve seen some simple one liner solutions for Self-Signed Certificates but none of them seemed to work for me. Whereas the above snippet of code has always worked. Obviously bypassing certificate validate is not something you want to run on a global scale in PowerShell but this code works great for your current session only.
If there is a simpler way to bypass certificate validation I’d love to hear it.
Often the TLS Version is also a problem.
My Code Snippet:
#region: Workaround for SelfSigned Cert an force TLS 1.2
add-type @”
using System.Net;
using System.Security.Cryptography.X509Certificates;
public class TrustAllCertsPolicy : ICertificatePolicy {
public bool CheckValidationResult(
ServicePoint srvPoint, X509Certificate certificate,
WebRequest request, int certificateProblem) {
return true;
}
}
“@
[System.Net.ServicePointManager]::CertificatePolicy = New-Object TrustAllCertsPolicy
[System.Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
#endregion
It works! Thanks a lot! 😀😀😀
worked perfectly, thanks!
Worked like a charm, thanks a ton!
flawless , thanks a bunch
Quick and easy solution for me too (AWS SAML behind seamless MITM enterprise proxy)
I’ve spend half a day trying to solve this issue before running on this post. This really is a quick fix, thanks!
How can I fix this and the server level permannently rather adding it in the each PS script. One command it will fix for all the scripts or request in the future.
thanks. 2019.03.
I use your code in my dockerless downloader
https://gitlab.com/Jancsoj78/dockerless_docker_downloader
Thanks a lot..! That was a Great help..! 🙂
Seriously dude I can’t thank you enough. Your syntax is exactly what i needed.
OMG, I search everywhere for this solution. Thank you!!!
works great thanks!!!!
It works! Thanks! 😀
thank you man !
thank sou so much
Perfect solution. Many thanks.
thanks -perfectly worked
Still relevant today.
TYVM!
Legend. Thank you for this article 🙂
its worked, thanks a ton